Who Are The Top Hackers In The World
In the article, you will find the Top Hackers In The World, but remember that the ranking list changes a few times in the year. Also, you will learn what types of hackers are there and who is in each category.
Hackers are actually Cyber pirates piqued by curiosity who break into your systems and challenge the privacy policies of the modern world.
This age is considered to be the safest as per privacy concerns when most of the web and apps claim to be protecting your privacy.
The worldwide web which has become a hub for storing information is merely a plaything in the hands of a few masterminds.
All they do is just throw malicious software into the system and gain access to their desired information.
Categories of the Hackers:
Hackers are labeled with respect to the color of the hat. There are three well-known categories of hackers: black hats, white hats, and grey hats.
Today the rainbow of hackers’ hats has broadened. The green hat, red hat, and blue hat have been included.
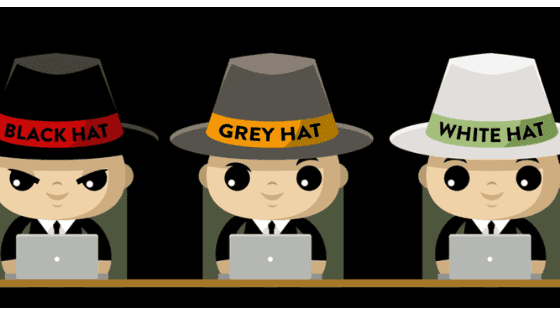
What’s the story behind these hats?
What’s the connection between these certain colors with types of hackers? why these colors are associated with hats? What’s the connection?
If the same questions surged into your minds then here is the answer.
These metaphorical terms originate from old spaghetti westerns, where the bad guys wear a black cowboy hat and the good guys wear a white hat.
The other nominated colors are some derivative terms coined later.
What All These Colors Actually Refer to?
- A black hat hacker is someone who malevolently exploits vulnerabilities in computer systems and networks.
- They use malware to cause harm. They are stereotypical hackers and often break laws for monetary gain and to cause cyber espionage.
- A white-hat hacker totally lies at the other side of the spectrum. They are the good guys of that old Western myth. They’re especially hired for ensuring cybersecurity. They are ethical hackers and assess the susceptibility of systems.
- Just like the color grey, a grey hat hacker is a fusion of white and black hats. They exploit vulnerabilities like black hats but they do it without any malicious intent just the way white hats do.
- Red hackers target to Linux system. Red hats have been characterized as vigilantes. They launch aggressive attacks against black hats. They mostly destroy the resources of black hats.
- Likewise, green hats are “wannabe hackers” wish to learn cybersecurity tricks, blue hats are the same as white hats employed to secure companies’ data and blue hats are revenge seekers, with no tendency towards learning.
Top Hackers:
1. Gary Mckinnon
Curious and restless in nature, a child has a keen interest in UFOs and is thought to get direct access to the channels of NASA. He installed some viruses and deleted a few files from NASA and the US military’s 97 computers. He declared the US military security as crap. He made an all–time biggest computer military hack.
2. LulzSec
LulzSec, a high-profile group of black hats hacked into accounts of the CIA, FBI, Scotland Yard, Sony News International, and other noteworthy accounts. The motto of the group “Laughing at your security since 2011” appears to convey its essence in a true way even now when the group has declared to be retired. There are statements about the group has hacked the websites of THE TIMES and THE SUN.
3. Adrian Lamo
Adrian Lamo, was a top-notch hacker who prevailed in the news when he hacked Google, Microsoft, Yahoo, and The New York Times but his disrepute fame resulted in his arrest. Later on, he got accompanied by a guy who was a spot on the hacker, hacking with the convenient environments of libraries, Internet cafes, and cafeterias but an overconfident guy called upon his doom by leaking several US government documents and was arrested Lamo managed to hide.
He was famous as a homeless hacker because of his fugitive lifestyle. In 2002, He broke into tons of internal systems of the New York Times. He gained access to private databases including the one that contained the information of 3000+ individuals.
He spent two years in prison for committing this crime and was fined approximately $65,000. In 2016, he came back into the news when he leaked important documents from the US Army.
4. Mathew Bevan and Richard Pryce
The target of the two partners was many great issues between the US and North Korea. The two hacked US military computers and used them to insinuate the foreign system. They tossed out the content from the Korean Atomic Research Institute into the USAF system. This caused a great rise to the massive International issue.
5. Jonathan James
The tragic story of Jonathan James ended with suicide. He started hacking at an early age and hacked many commercial government networks. He hacked NASA’s Network, downloaded source codes, and learned about the working system of NASA’s space station. In 2007, many high-profile companies were hacked. However, James renounced his involvement. He committed suicide due to being suspected and interrogated.
The story of James is very heartbreaking. He started hacking at a very young age and succeeded to break into a lot of government and commercial networks. For committing all of these serious crimes, he was sent to jail. Now, the world knows him as “c0mrade”.
He hacked the computer network of NASA and copied sufficient source code to get information on how the international space station worked. NASA had to shut down the network for 21 days while they were investigating the security violation. They had to bear the loss of more than $1.7 million.
In 2007, he was suspected of attacking the networks of various top companies. However, he denied his involvement in all the hacking activities, but he was investigated. He committed suicide in 2008.
6. Kevin Poulsen
Kevin Poulsen hacked the radio station’s phone lines and fixed himself as the winner caller just so he could win a Porsche. Later on, he was arrested by the FBI for money laundering, wire and computer fraud. He was sentenced to prison but after his release, he now serves as a journalist.
7. Kevin Mitnick
Today’s affluent entrepreneur was once the most wanted cyber–criminal. He was convicted of hacking Pentagon, Motorola, and Nokia. He was found guilty of computer fraud, wire fraud and illegal interception of a wire communication. After five-year imprisonment and eight months of solitary confinement. He turned out to be a security consultant.
8. Anonymous
A “ hacktivist group” endorsed themselves by targeting religious, government, and corporate websites. The Vatican, the Ugandan government, the FBI, the CIA, PayPal, and Mastercard have been their scapegoats. They are also named as digital Robin Hood. They would appear in public wearing marks.
9. Astra
Astra was a hacker who haggled with weapons. He took the Sanskrit word Astra as his pen name which meant weapons. He hacked into the system of France’s Dassault Group and stole their weapons and data. He told it out skilfully to different countries and remained untraced.
10. Albert Gonzalez
The biggest credit card to be recorded in history was one of the netizens’ credit cards. Albert Gonzalez made history by reselling 170 million credit cards and ATM numbers. When he was arrested he was sent to Federal prison for 20 years.
This Might Be Important
Hackers whether putting a question mark on your security or being pioneers to seek new ways to cyber technology are not good or bad they are just smart so what’s your definition of hackers? Decide it yourself.
Top Hackers In The World

In the world of the internet where we get connected globally, it is really easy to break into someone’s private zone without his permission.
By private, we don’t mean just social media, but many other things.
The world wide web has become the heart of storing and restoring data because it is perceived to be a secure vault.
However, it is a mere toy in the hands of a few networking and computing professionals that are known as hackers.
There are many other names that are used for recognizing them such as villains, crackers, geniuses, criminals, and cyber-pirates.
They are the experts of black hat hacking techniques and they just throw a malicious program or a virus at a system to gain unauthorized access to the desired data and emails.
Due to their extreme curiosity, they may also break into your computer system, to cause you a lot of harm.
But, don’t worry because not all cyber-criminals are bad.
The good ones are known as white-hat hackers and they use hacking techniques and tools for the improvement of computer security.
In this post, we have crafted a list of top hackers and influential people who put the world in awe with their extraordinary abilities.
11. Kevin Mitnick
He is probably one of the best hackers in history. He has been declared as “the most wanted cybercriminal in the USA” by the FBI. The self-styled guy arrived in the black-hat hacking world when he was a teenager.
He has hacked the sensitive data of lots of corporations and technology and telephone companies including Motorola, Nokia, and many others. In 1995, after a high-profile pursuit by the FBI, Kevin was arrested. He was released from prison after 5 years in 2000.
When he was released from jail, two very influential US Senate members requested him to test the computer systems of the federal government for enhanced security protection.
This was the time when he left the world of black hat hacking and started offering computer security consultancy services.
Now, he is a bestselling author, commentator, and cybersecurity speaker who is helping companies to resist social engineering.
12. Gary McKinnon
In this childhood, he was reportedly a curious and agitated child. To collect information on UFOs, he preferred to gain direct access to the networks of NASA.
He penetrated the computer systems of the US Army and NASA by deleting some files and by installing a virus from his girlfriend’s aunt’s house in London.
He did all of these efforts just to satisfy his adventurous soul, but he was soon found guilty of hacking the websites and computer networks of NASA and the US Army.
Entering and deleting the files was not enough for him, so he thought of humiliating the US Army by leaving a note that said “Your security is crap” on their website.
He was able to shut down the largest military computer network of 2000 computers for more than one day.
13. Robert Tappan Morris
He was the son of a cryptographer who served NASA for many years. He is known as a person who unintentionally violated the internet. He wrote a program for traveling from one system to another that became the first computer worm.
He gained illegal access to many computers and to distribute the worm to other computers, he used MIT’s systems which also helped him to hide his location.
The actual purpose of his program was to determine if the computers were already infected or not. The worm spread rapidly, then he sent alert messages to the computer admins, but it was too late.
His program infected more than 6000+ systems and it was the first DDoS attack of history. The victims spent a heavy cost for removing the infection from their computers.
After this event, Morris was arrested, but lawyers took 8 months to prove that he was responsible for attacking the systems. He was the first hacker who faced trial under the computer fraud and abuse act.
Now, he is a well-known and reputable lecturer at the Massachusetts Institute of Technology. He is the co-founder of Y Combinator company which provides funds to new startups.
How Can I Protect My Smart Devices from Top Hackers?
Protecting your smart devices from top hackers is crucial in today’s digital era. Simplify smart world with no code iot systems offer an effective solution. By implementing robust security measures, such as strong passwords, regular software updates, and utilizing virtual private networks (VPNs), you can fortify your devices against potential cyber threats. Stay proactive and prioritize security to safeguard your connected devices.
Should I Watch the Top Hacking Movies if I’m Interested in Learning About Real Hackers?
Interested in learning about real hackers? Wondering if you should watch hacking movies to gain insights? While movies can offer entertainment value and inspire curiosity, it’s essential to remember that they often sensationalize hacking. For a more accurate understanding of the subject, engaging with reputable educational resources, books, and documentaries would be more beneficial than solely relying on hacking movies to watch.
14. Guccifer
He is a well-known hacker who revealed the existence of Hillary Clinton’s private email server. He broke into the systems of numerous American political personalities. Guccifer was the first person who leaked the photographs of former president George Bush’s paintings.
He has hacked the personal email and social media accounts of former Secretary of State Colin Powell. The US government deported him from Romania in March 2016.
If you are scared that a hacker will break into your system and will ruin your life, then don’t worry because usually, they go after high-profile corporations and personalities.
To stay protected, you must use security software that will guard your system against viruses and malware.




0 Comments